Fill out the form to get more information about the Fullstack Academy bootcamp of your choice.
04.24.2025
Types of Social Engineering Attacks and Prevention Tips
By The Fullstack Academy Team

Being on the receiving end of a social engineering scam is no joke. “Social engineering” refers to scams hackers use to fool individuals into sharing personal details to sabotage or steal their information. This type of activity is at the heart of many cyberattacks. By 2025, cybercrime will cost the world $10.5 trillion yearly. According to Comparitech, more than 71.1 million people are victims of cybercrime like social engineering each year. However, social engineering does not take place online only.
In fact, one of the best-known instances of social engineering, dating back nearly a century, did not require any advanced equipment or technology. In 1925, Victor Lustig, from the present-day Czech Republic, posed as a high-ranking Parisian official to “sell” the Eiffel Tower. By the time the would-be buyer, André Poisson, realized he’d been duped, Lustig—along with Poisson’s money—had already left France.
Victims of online social engineering attacks can suffer a similar fate if they provide information to someone pretending to be a trusted individual or from a reputable organization. If successful at gaining their trust, the scammer may seek to access the victims’ data or money or may install malware that disrupts their computers.
Due to the prevalence of these threats, employees who provide security against them are in high demand. According to cyber talent shortage data from CyberSeek, there were 457,433 openings in 2024 requesting professionals with cybersecurity-related skills, with employers struggling to find candidates who possess them. Filling the average cybersecurity role takes 21% longer than other IT jobs.
Ready to jumpstart a career in cybersecurity?
Learn the skills you need to fight cybercrime with our part-time and full-time bootcamp offerings
Read on to learn more about social engineering attacks and how to avoid becoming a victim. In this article, we’ll explore:
What Is Social Engineering?
Sometimes called human hacking, social engineering preys on victims’ thoughts and actions. Criminals use the psychology of persuasion to lead people to unwittingly make unsafe decisions. With cybercrime, the person behind the attack may use an official-looking email, for example, to solicit an action from the recipient to gain access to private information, valuables, or money. If the fake email convinces the recipient of its legitimacy, the recipient may respond by providing that access.
Aon, a professional services company, reports that humans’ innate desire to be helpful puts them at risk of social engineering attacks. Increased physical security measures have driven many social engineering criminals online, where they can more easily access people—and prey on their tendencies. Additionally, as more work and personal activity moved online during the COVID-19 pandemic between 2020 and 2021, material breaches online increased by nearly 21%, according to research firm ThoughtLab.
What Is a Social Engineering Attack?
Social engineering attacks involve manipulating people’s emotions to persuade them to violate security procedures and best practices. The perpetrator then uses this lapse to gain unauthorized access to systems, networks, or facilities.
Social engineering attacks as we know them today started in the 1990s when criminals began calling people and tricking them into providing their corporate online credentials or dial-in information. The criminals then used that access to send the company’s money to offshore bank accounts, sometimes costing the company millions of dollars and leading employees to lose their jobs.
Social engineering attacks have become a significant problem for individuals and companies. According to Sprinto.com, 98% of cybercriminals today use social engineering techniques to exploit human vulnerability and gain access to sensitive data.
When one individual falls prey to a social engineering attack in an organization, it can affect the entire company.
Four Steps of a Social Engineering Attack
The process that social engineering attackers use to persuade people to take a specific action includes four basic steps. These steps may occur in a single interaction or take months as a full social engineering lifecycle.
Below are the steps of this type of attack.
1. Research
Initially, a social engineering attacker gathers information about the potential victim. This step could include face-to-face interaction, such as striking up a conversation about work. However, more often today, criminals conduct this research through software that finds personal information about the targeted individuals. They also can find information in a target’s social media accounts and by purchasing personal information on the dark web.
2. Build Trust
After learning about the character and habits of the targeted individuals, social engineering attackers work to build their trust. They can send online messages, impersonate co-workers, and make up stories to convince the potential victims to believe them.
3. Find a Weakness
Once they exploit the trust of the targeted individuals, they find the sources for private information that are most vulnerable—including those with credentials, banking details, and permissions—and then trick the individuals into providing access to those sources. To coax someone into providing access to personal or corporate information, criminals may rely on tactics such as:
Playing on emotions—threatening the loss of an account unless the person provides credentials
Sending a request from a “friend”—gaining access to a person’s email or social media accounts and sending messages that appear to come from the person
Using similar email addresses—sending a message from an account whose email address is similar to an official address
Promising compensation—offering a pricey item in exchange for information or money
4. Disengage
As soon as the social engineering attacker completes the desired action and collects the information or money they were seeking, they end the interaction and disappear—removing any trace of malware and evidence of social engineering activities.
How Do You Identify Most Types of Social Engineering Attacks?
Although identifying a social engineering attack may seem daunting, all is not lost. The first thing to remember about these attacks is they adhere to a specific pattern. So, once you familiarize yourself with the warning signs, you can effortlessly and quickly spot the frauds.
Here are the characteristics you should look for:
Amateurish typos and other egregious errors. Many perpetrators of social engineering attacks have less than stellar command of the English language. For instance, “Microsoft” didn’t release Office 365! Watch for spelling and grammatical errors that a professional organization wouldn’t commit.
- The usual phishing subject lines. Scammers want you to act before thinking, so they incorporate alarming, provocative subject lines. Here’s a sample of effective scam subject lines you will undoubtedly trip over often:
Notice of payment
FBI letter of notification [code 210]
Notice: Your online account was accessed
Re: Your installation
Confirmation for your delivery
Messages that elicit a knee-jerk emotional response. Building off the previous point, scammers try to incite emotions such as greed, fear, excitement, and curiosity. When you read an online offer or e-mail that seems too good (or awful) to be true, pause, take a breath, and look at it closer. Don’t simply react. Allow your common sense time to weigh in.
Impersonators. Sometimes, social engineering attackers pose as someone you know, work with, or conduct business with. Remember, reputable agents never ask you for sensitive information by e-mailing or calling. If something about the exchange doesn’t seem right, end the communication, then immediately call the person the first party claimed they were.
Ransomware. Some hackers try to extort money from you by locking up your files, data, or even your device. It’s typically presented as a virus warning that requires you to pay a fee to get your system cleaned up. If you believe you’re a ransomware scam or identity theft victim, notify the FBI in the former case and your local law enforcement in the latter case.
Who Are the Primary Targets of Social Engineering Attacks?
Social engineering attacks aim to access sensitive information like bank accounts, company data, or Social Security numbers. The more access a target has to what cybercriminals want, the more attractive the target becomes.
Consequently, the most frequent targets of social engineering attacks include:
Popular online personalities. People such as YouTubers and influencers who share more personal information online are more likely to be targeted. For example, if your son has 150k Instagram followers or your daughter runs a successful, popular podcast, they could be targets.
High-profile employees, high-worth individuals, and high-level leaders. Criminals prefer targets with high levels of access.
Younger people and employees who are unaware of cybersecurity threats. Kids lack worldly experience and thus are more vulnerable to getting manipulated online. Additionally, many employees aren’t well-informed on today’s cybersecurity threats such as phishing or malware.
Types of Social Engineering Attacks
According to Yahoo Finance, the global digital storage devices market is projected to expand from $4.5 billion in 2024 to $14.0 billion by 2033, indicating a CAGR of 13.4%. In 2023, the FBI received a record-breaking 880,418 reports of Internet crimes, with losses exceeding $12.5 billion, a 22% increase in financial losses from 2022.
Key Online Origins of Social Engineering Attacks
Among the biggest sources of information for social engineering attacks are social media, email, forums, group chats, and other messaging platforms. Below are some examples of how people who plan to use social engineering can glean information from these online sources.
Social Media
Social media posts can reveal various details about an individual, and cybercriminals can scan and collect that information to find and engage with social engineering victims. For example, they may see a company’s strategic information in an employee’s posted photo from a meeting. They may collect data such as a person’s job, interests, and background from social media activity.
Email is another popular source social engineering attackers use to collect information. In emails that appear to be from a trusted friend or company, they use tactics such as:
Including a link or attachment with malware
Telling a fabricated story about an emergency and asking for help
Seeking a donation to a bogus fundraiser
Asking the recipient to verify account information by clicking a link
Falsely claiming that the recipient is a prizewinner and must provide information to claim it
Ready to jumpstart a career in cybersecurity?
Learn the skills you need to fight cybercrime with our part-time and full-time bootcamp offerings
Forums and Group Chats
Criminals can seek out potential victims in online forums and group chats, attempting to befriend people in the chat sessions based on the details they learn about them. Another social engineering tactic for online forums is targeting the hosts of websites where these discussions occur to gain user information.
Thirteen Social Engineering Types
From methods that employ electronic messaging to those that rely on phone calls or personal contact, social engineering techniques run the gamut. Below are 13 common types of social engineering scams.
1. Phishing
One of the most common forms of social engineering attacks is phishing. In this type of attack, the cybercriminal sends an email or a text disguised as legitimate and from a trusted source. The goal is to trick the recipient into providing information or clicking a link. The attacker can then gain access to data or money or launch malware on the recipient’s device.
2. Pretexting
With pretexting, a social engineering attacker scams someone to gain access to data. In messages that appear to be from a co-worker or from law enforcement or financial officials, the attacker often asks for confirmation of private information, purportedly to allow the employee or official to complete an important task.
3. Whaling
Whaling—a larger-scale form of phishing—targets high-profile figures with access to more privileged or valuable data, such as CEOs, chief financial officers (CFOs), or government officials.
4. Baiting
Attackers use baiting to capitalize on a person’s greed or curiosity by leaving a computer item, such as a flash drive, with malware on it for someone to find. By taking the device and inserting it into a computer, the person unintentionally installs malware. Another approach to baiting involves placing ads that entice people to click a link or download an application that installs malware.
5. Quid Pro Quo
Quid pro quo is the practice of a social engineering attacker pretending to offer something in exchange for the targeted individual’s assistance. With this type of social engineering attack, the perpetrator asks for information to provide assistance, such as information technology (IT) help, to the victim. The perpetrator then uses the information to gain access to private information or install malware.
6. Watering Hole
The watering hole method combines social engineering with hacking. The attacker hacks a website that the targeted individuals frequently visit and trust. The attacker then infects the trusted website with malware or inserts links that the targeted individuals click on when they visit the website.
7. Tailgating
Sometimes called “piggybacking,” tailgating is a form of social engineering attack that occurs when the criminal closely follows someone into an unauthorized physical location—or uses trickery to gain entrance. The criminal then gains access into the area along with the person.
8. Scareware
Attackers use scareware to dupe someone into believing a device has been infected with malware or illegal content. The attacker then offers a solution to the “problem” that involves unknowingly downloading real malware or purchasing unnecessary services.
9. Spear Phishing
Spear phishing is another targeted form of phishing. In this type of attack, the perpetrator chooses specific individuals or organizations, tailoring the messaging to mimic a typical message that the target might receive and using job titles or contacts that make it appear legitimate. The message directs recipients to change their password and sends them to a page that collects their credentials.
10. Honey Traps
Posing as someone with whom the recipient may want to pursue, the attacker uses a “honey trap” to lure the targeted individual. Feigning interest in a relationship, the attacker tricks the person into sharing information.
11. Vishing
Vishing, also called voice phishing, uses phone calls. The social engineering attacker contacts an individual by phone and scams the individual into providing sensitive financial or personal information.
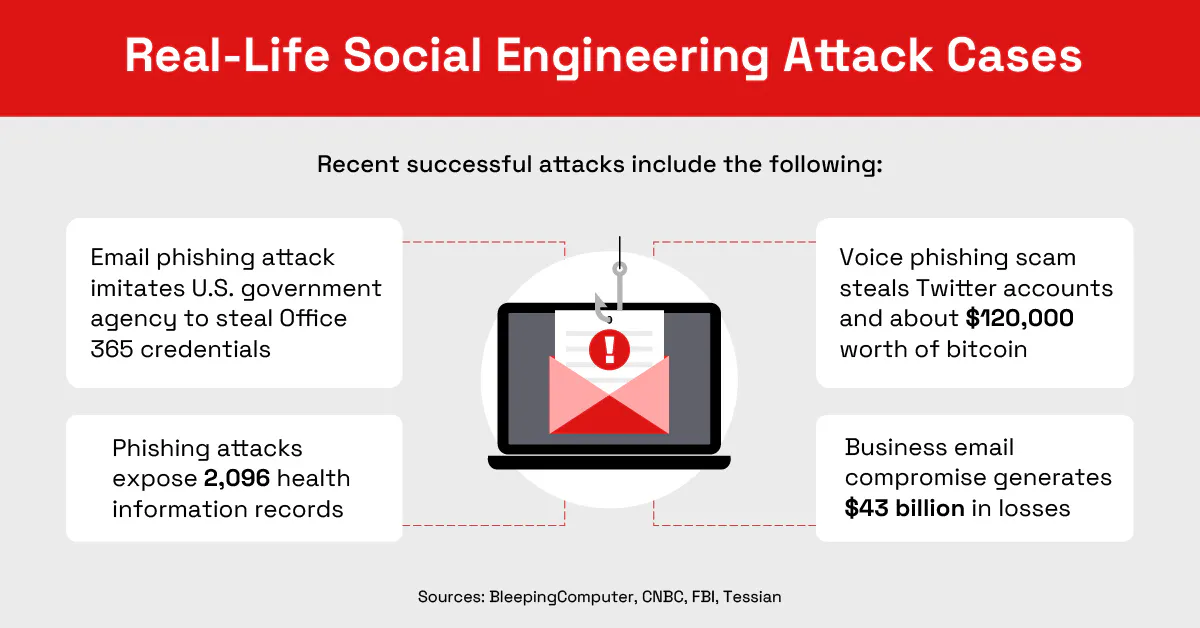
12. Business Email Compromise
Business email compromise (BEC) attacks targeted individuals or small groups within a company, with the criminal posing as someone of authority in that organization or a partner organization. The message might come from a fake or hacked email account or from an email address that is similar to a real one.
13. Angler Phishing
With angler phishing, the victim is someone who complains about a service on social media. After seeing the complaint—especially if it involves access to financial information—an attacker will quickly establish a fake account on that social media platform. Using that account, the attacker reaches out to the person who posted the complaint and poses as customer support for the organization. The attacker then asks for the person’s access information to “fix” the problem.
More Information About Types of Social Engineering Attacks
Additional information about different social engineering attacks is available in online and print sources.
Aura, “12 Latest Types of Social Engineering Attacks (2022)”: This resource describes forms of social media attacks and provides tips about what to watch for, including common scam email subject lines.
BeyondTrust, “The 10 Most Common Social Engineering Attacks”: This resource lists types of attacks and explains the risks that they pose.
BioCatch, “Types of Social Engineering Attacks: Detecting the Latest Scams”: This resource explores criminals’ techniques for social engineering attacks and how to recognize them.
Dummies, “Types of Social Engineering Attacks”: This resource provides an overview of the ways social engineering attackers attempt to dupe victims.
Social Engineering Attack Examples
Social engineering is dangerous not only because they prey on universal user activity, but because the attacks are constantly evolving.
With every new technology trend comes the risk of social engineering scams to capitalize on it. Social engineering attacks through social media and web applications, for example, have become common threats. Also among the top emerging cyber threats are attacks that use deepfakes: artificial intelligence (AI) versions of people.
Recent Examples of Social Engineering Attacks
Recent examples of social engineering attacks have shown how the practice continues to prey on natural human behavior—and ever-changing technology tools and techniques.
Bitcoin Scam Through Social Media
Through phishing that relied on Twitter direct messages, a social engineering attacker snagged $121,000 in bitcoin by taking over the accounts of about 130 people in 2020. Among those with compromised accounts were politicians and business leaders, and one direct message came from the account of an elected official in the Netherlands.
Russian Hackers Target Ukraine Via Phishing Attack
In 2022, the Russian-based hacker group Gamaredon launcheda six-month assault on several Ukrainian entities. The attacks targeted the Ukrainian military, government, non-government organizations (NGOs), law enforcement, judiciary, and non-profit organizations. The main goals were to exfiltrate sensitive information, maintain access, and leverage it to move laterally into related organizations.
CEO Vishing Attack
A 2019 scam used vishing, whaling, and an AI voice to con a U.K. energy firm executive into transferring $243,000 to an individual who the CEO believed to be the boss. After the transfer of funds, the attacker called back, again using the AI voice, to falsely promise reimbursement of the funds.
Department of Labor Fake
In 2021, a cybercriminal posed as the U.S. Department of Labor (DOL) in a phishing attack to grab business account information from unsuspecting people. Using domain names that were the same, or similar to, those of the DOL, the attackers invited people to bid on fake projects. As part of the bidding process, the individuals had to provide their Microsoft accounts or other business account information, which the attackers stole. If would-be bidders tried to enter those credentials again, the attackers sent them to the legitimate DOL website.
Health Information Theft
Five government employees in California were victims of phishing in 2021, providing login credentials to social engineering attackers by clicking an email link that took them to a malicious website. With the supplied user information, the attackers accessed nearly 3,000 records with health information and more than 800 records with personally identifiable information (PPI)—leaving the government at risk for lawsuits for breaching the Health Insurance Portability and Accountability Act (HIPAA).
Social Engineering Prevention Tips
Cybersecurity professionals can help protect individuals and companies from the many types of social engineering attacks. Individuals in this role build, test, and analyze systems to protect others against cyberattacks, including attacks that rely on social engineering.
Ready to jumpstart a career in cybersecurity?
Learn the skills you need to fight cybercrime with our part-time and full-time bootcamp offerings
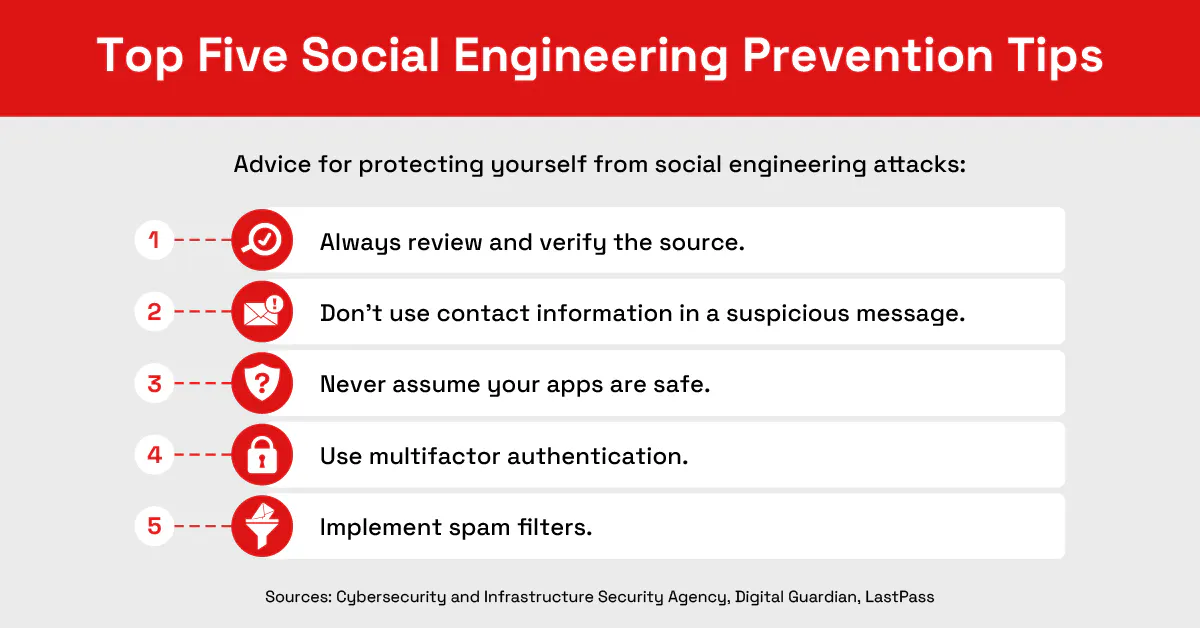
People can help protect themselves from social engineering attacks too. Following these social engineering prevention tips can help them avoid taking the actions that can lead to security problems:
Review and verify the source. Check domain names by typing them into a browser.
Do not use contact information in a suspicious message. First, confirm the message’s authenticity by voice or video call.
Never assume your apps are safe. Always take precautions in the event of a cyberattack.
Use multifactor authentication. Add a layer of protection against unauthorized access, such as MFA.
Implement spam filters and anti-phishing features. Identify messages that are likely to be spam or phishing attempts.
Use a virtual private network. Encrypt your Internet activity and disguise your identity in public places with a VPN.
Monitor your accounts closely. Identify unwanted changes quickly.
Use cybersecurity software. Perform security updates regularly.
Keep software up to date. Ensure that your software is protecting against new risks.
Do not click links that you did not request. Verify the source of the message.
Limit the personal information you share online. Protecting username, password, date of birth, SSN, and financial data.
Recognize and Protect Against Social Engineering Attacks
With Internet crimes reported to the FBI in 2021 leading to more than $6.9 billion in potential losses, it pays to be vigilant about protection against these attacks—including those from social engineering attackers.
Learning about the types of social engineering attacks, staying up to date on cybercrime techniques, and following social engineering prevention tips can help people and companies avoid the many security and financial issues that often result from these attacks.
Infographic Sources:
BleepingComputer, “Office 365 Phishing Attack Impersonates the US Department of Labor”
CNBC, “Twitter Says Hackers Accessed Direct Messages of 36 victims, Including One Elected Official”
Cybersecurity & Infrastructure Agency, "Security Tips"
Digital Guardian, “Social Engineering Attacks: Common Techniques & How to Prevent an Attack”
Federal Bureau of Investigation,”Business Email Compromise: The $43 Billion Scam”
LastPass, "How to Protect Yourself from Social Engineering Attacks"


